Detecting Cyber-Attacks in Cyber-Physical Systems

Purchased on Istockphoto.com. Copyright.
Cyber-attacks can alter the behavior of sensors and actuators in industrial plants and other connected systems. Thus, it is essential to detect cyber-attacks before they compromise normal operations of systems and cause damage to physical objects and even safety risks. We propose FID-GAN, a novel intrusion detection system (IDS) that detects cyber-attacks when other security mechanisms, such as firewalls and authentication, fail to block them. Our solution does not require data from attacks, which is difficult and sometimes impossible to obtain as new types of attacks come up every day. In addition, it achieves higher detection rates, and is at least 5.5 times faster than a baseline IDS. Keywords: Cyber–physical systems (CPSs), industrial security, intrusion detection systems (IDSs), machine learning, generative adversarial networks (GANs).
Introduction
Cyber-physical systems (CPSs) integrate computing and physical processes to effectively control systems through computation, efficient communication, and connected sensors and actuators [1]. They enable remote access and control of systems, devices, and machines, putting together physical processes, such as sensing and computing, which analyze data to make decisions. Thus, CPSs are essential in industrial environments, especially for Industry 4.0 [1], [2]. However, their widespread adoption introduces several security threats that may cause inaccurate sensing and actuation. Such misbehavior can lead to severe damage to the controlled physical objects and harm the people who rely on them [2], [3].
Intrusion detection systems (IDSs) detect cyber-attacks that other security mechanisms, such as firewalls and authentication, could not prevent. Advances in artificial intelligence and deep learning foment new IDSs that can handle the current cyber-attacks level of sophistication and complexity [4], [5], [6]. However, obtaining attack samples can be very time-consuming and sometimes even impossible due to new types of attacks that come up every day. Thus, IDSs that do not rely on such attack data are preferable [7]–[9]. Moreover, reducing detection latency—the time interval between the start of an attack and its detection—is a critical challenge [10]. For instance, IDSs that detect attacks on industrial plants only after damages have occurred do not fulfil their purpose. Hence, IDSs need to detect cyber-attacks quickly enough so that damage is prevented.
Detecting Attacks with FID-GAN
We propose FID-GAN, a novel IDS for CPSs that does not rely on attack data and detects attacks faster than other state-of-the-art IDS solutions. Our solution uses only normal data—data obtained from the regular operation of systems—and a generative adversarial network (GAN), a framework that trains two competing neural networks called generator and discriminator. The generator learns to synthesize normal data, and computes a reconstruction loss, LR, which measures the difference between a data sample under evaluation and a similar sample that it produces. On the other hand, the discriminator learns to distinguish between normal data and anomalies by computing a discrimination loss, LD, which measures the probability that a sample represents an anomaly. FID-GAN combines LR and LD into an attack detection score that represents how likely a sample under analysis is an anomaly. In contrast to other works, we trained a third neural network that accelerates LR’s computation, and thus the attack detection score used to detect cyber-attacks.
To further accelerate attack detection, our IDS is deployed in three layers: 1) end point layer, 2) fog layer, and 3) cloud layer. The end point layer is where CPSs are located. It is from this layer that the normal data patterns used to train the neural networks come from. The unknown data patterns that are evaluated by our IDS also come from the CPSs in this layer. The Cloud layer is endowed with more computing resources, and it is where training of the neural networks takes place. Finally, the fog layer is where the proposed detection system is deployed. Since it is closer to the CPSs in the end point layer, lower latency is achieved, which is suitable for the real-time requirements of attack detection. Figures 1 (a) and 1 (b) show the training and detection models of FID-GAN.
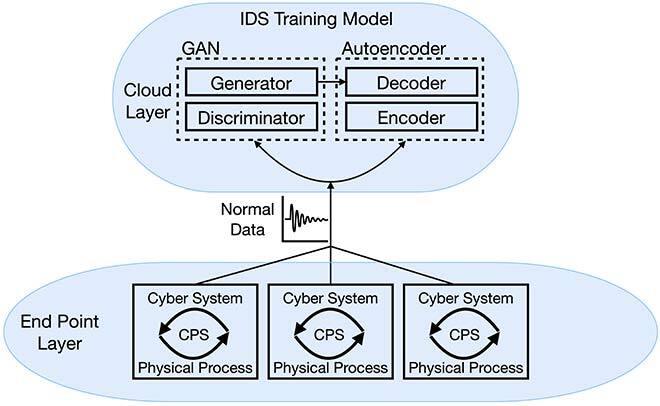
Fig. 1 (a) FID-GAN Training Model
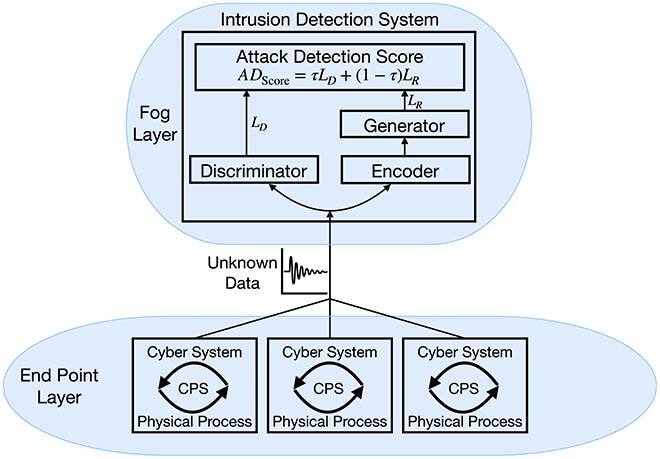
Fig. 1 (b) FID-GAN Detection Model
Efficacy and Efficiency of FID-GAN
We evaluated both the detection rate and latency using three public available datasets: NSL-KDD [11], SWaT [12] and WADI [13]. While NSL-KDD contains network traffic data and attacks, SWaT and WADI contain sensor measurements of a water treatment plant. We compared the area under the curve (AUC) of the receiver operating characteristic (ROC) of FID-GAN with two state-of-the-art IDSs that also use GANs: multivariate anomaly detection with GAN (MAD-GAN) [14] and adversarially learned anomaly detection (ALAD) [15]. Figures 2, 3 and 4 show that our IDS is more accurate than MAD-GAN and ALAD in the three datasets. In addition, Figure 5 shows that our IDS is at least 5.5 times faster than MAD-GAN. Although ALAD achieves the shortest detection latency among the three IDSs, it is less accurate in detecting attacks in the two datasets with sensor measurements. Therefore, our IDS is the most suitable to detect cyber-attacks in CPSs among the three IDSs studied.
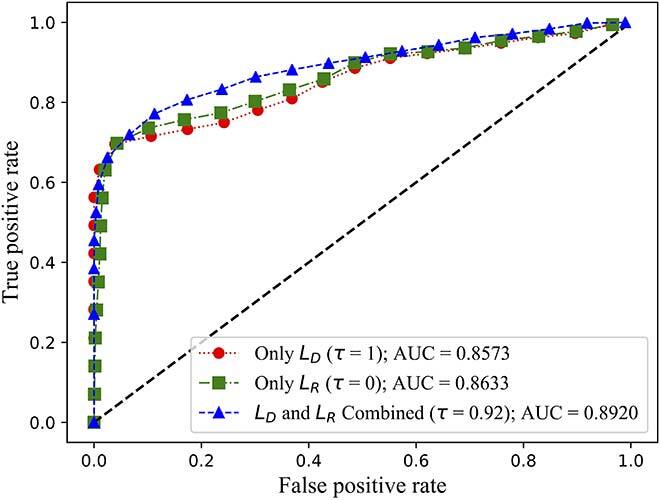
Fig. 2 (a) ROC curves of FID-GAN on the SWaT dataset
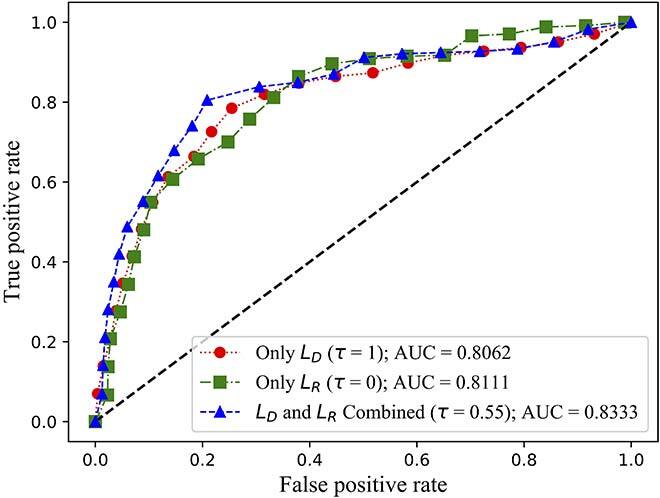
Fig. 2 (b) ROC curves of FID-GAN on the WADI dataset
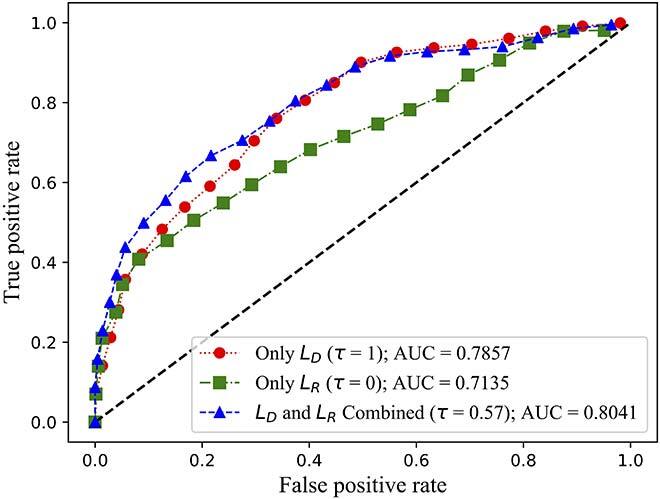
Fig. 2 (c) ROC curves of FID-GAN on the NSL-KDD dataset
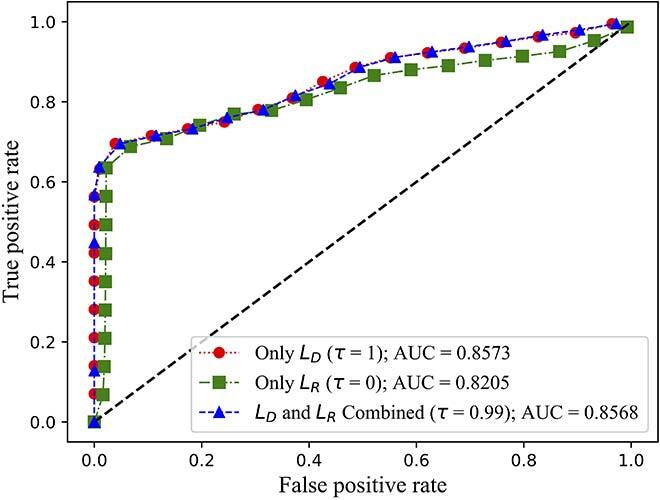
Fig. 3 (a) ROC curves of MAD-GAN on the SWaT dataset
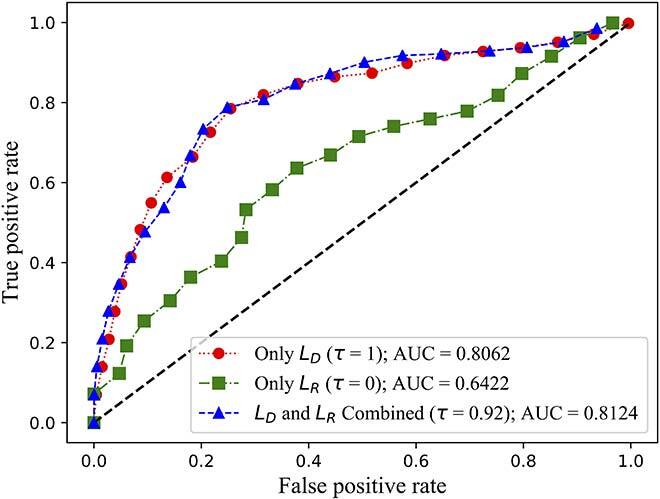
Fig. 3 (b) ROC curves of MAD-GAN on the WADI dataset
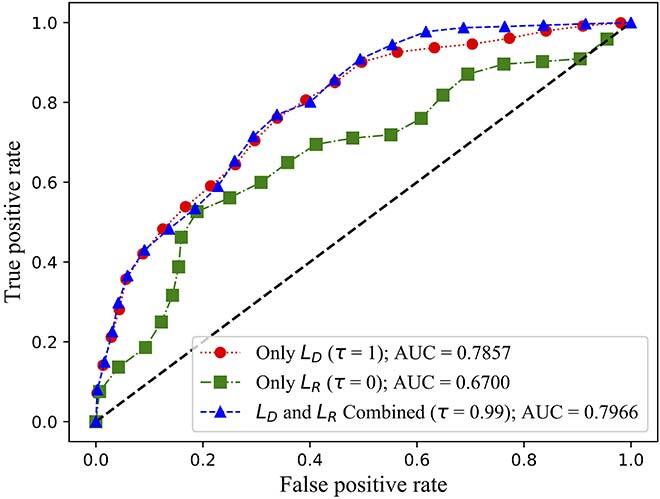
Fig. 3 (c) ROC curves of MAD-GAN on the NSL-KDD dataset
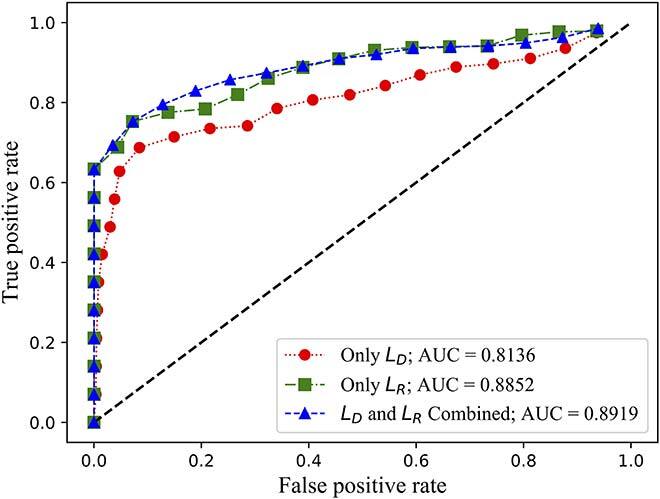
Fig. 4 (a) ROC curves of ALAD on the SWaT dataset
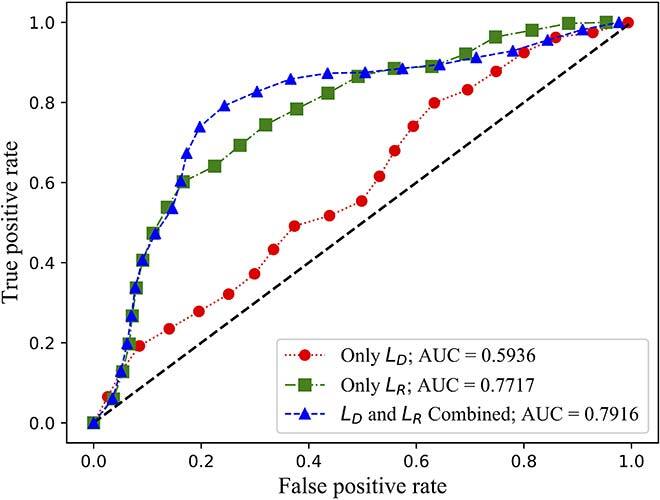
Fig. 4 (b) ROC curves of ALAD on the WADI dataset
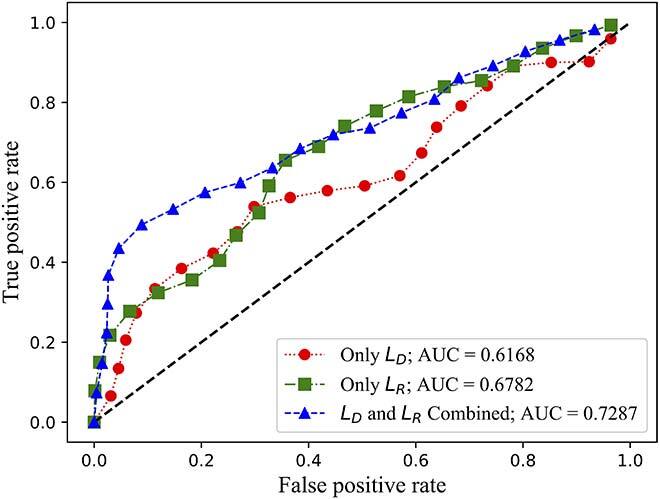
Fig. 4 (c) ROC curves of ALAD on the NSL-KDD dataset
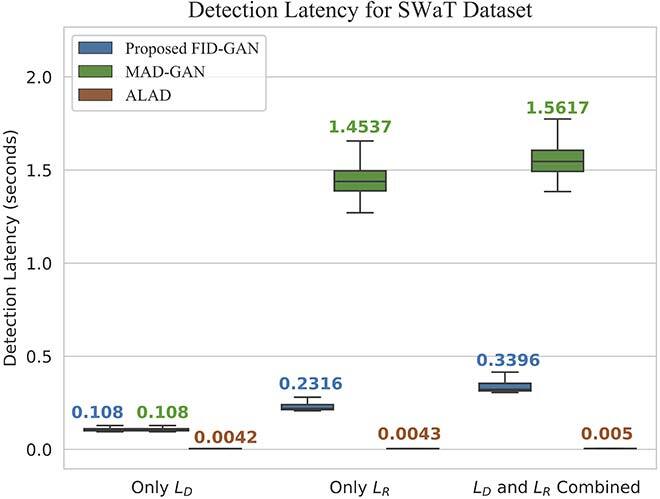
Fig. 5 (a) Detection Latency on the SWaT dataset
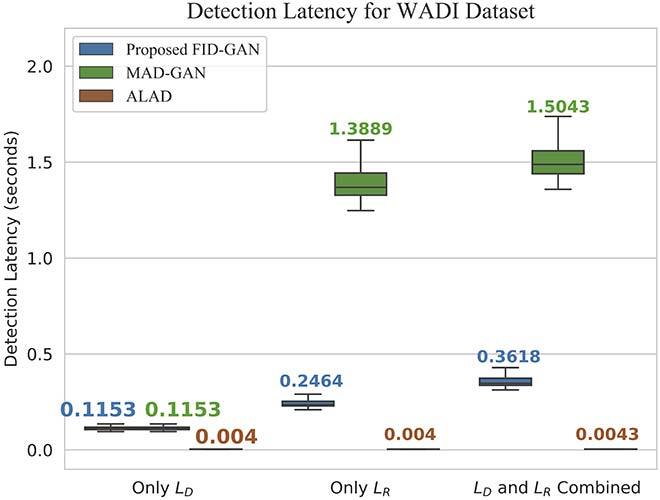
Fig. 5 (b) Detection Latency on the WADI dataset
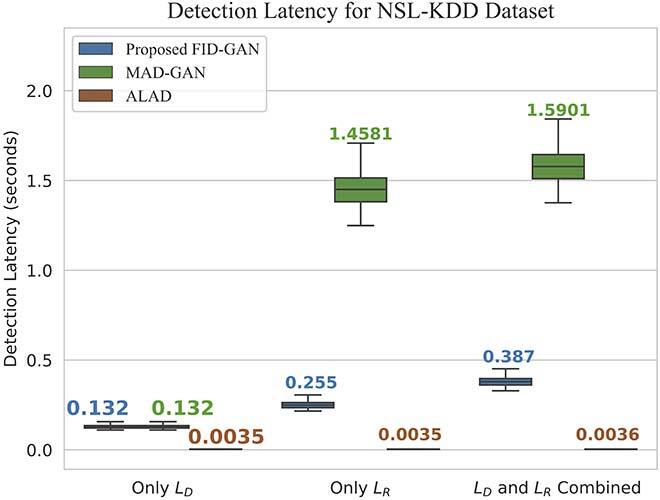
Fig. 5 (c) Detection Latency on the NSL-KDD dataset
Conclusion
We propose a novel IDS for CPSs using GANs that outperforms two state-of-the-art IDSs and is at least 5.5 times faster than one of them in detecting cyber-attacks. Such a reduction in detection time is very impactful as it is necessary to detect attacks fast enough so that reaction techniques have time to prevent damage. Thus, our work contributes to securing cyber-physical systems in many industries and even automated systems in our homes.
Additional Information
For more information, please read the following research paper: P. Freitas de Araujo-Filho, G. Kaddoum, D. R. Campelo, A. Gondim Santos, D. Macêdo and C. Zanchettin, “Intrusion Detection for Cyber–Physical Systems Using Generative Adversarial Networks in Fog Environment,” in IEEE Internet of Things Journal, vol. 8, no. 8, pp. 6247-6256, 15 April15, 2021, doi: 10.1109/JIOT.2020.3024800.



